CSE190/291 – Wireless & The IoT
Lab 1: Playing with your local network
The purpose of today’s lab is to solidify your background in the ‘nuts & bolts’ of Internet technologies, and to give some empirical experience in ‘peeling back layers’ of the Internet.
This should hopefully be a fun bit of poking around with what your computer is actually doing all the time — for better or worse, I always find something new every time I look at the firehose of packets coming in and out of my machine #NotASecurityProfessor.
PreLab
First, make a copy of the PreLab Report Document to fill in as you work.
A. Install Wireshark
We will use Wireshark, available here. Follow the installation instructions to set up wireshark on each group members' machine.
Sometimes, you can run into some permission headaches getting wireshark access to your network traffic. The modern installer is pretty good at getting all the permissions it needs, but if you have issues, Google is going to be a better bet for debugging than staff probably.
It is not a good idea to run Wireshark as root — it’ll get all the packets, sure, but that’s really opening yourself up for trouble #OkayIDoListenToTheSecurityProfessorsSometimes.
There is no deliverable for this section.
B. Get comfortable with Wireshark
When you start Wireshark, you have to tell it where to capture packets from. In practice, this is a list of cryptic, short names; e.g. here’s what I see:
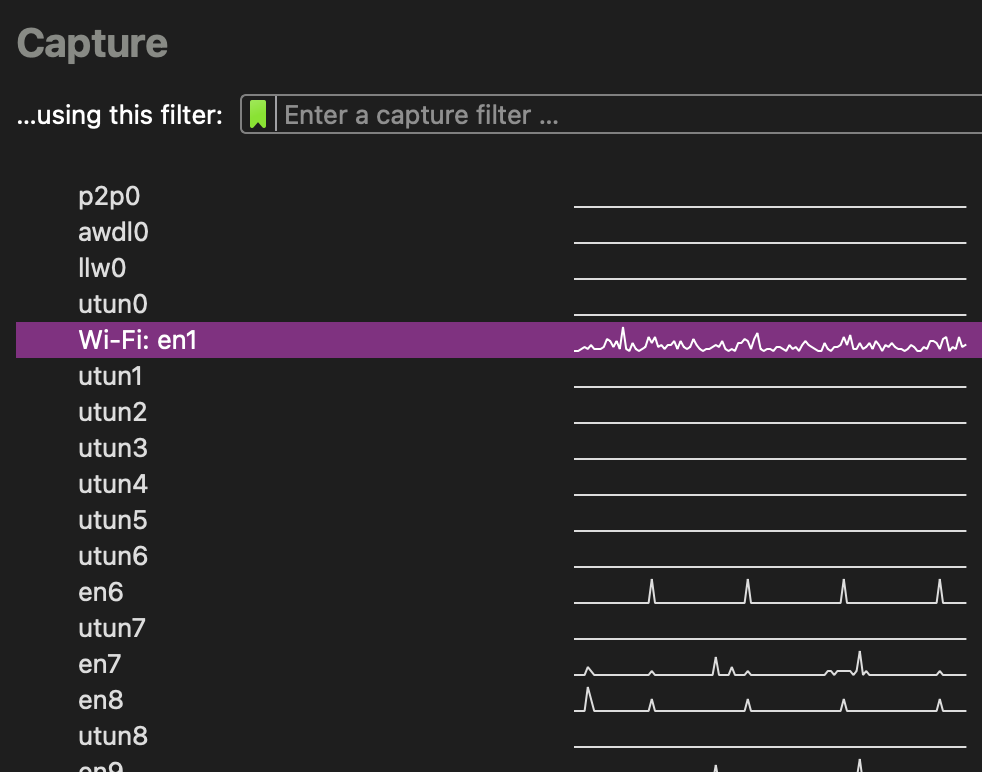 I have active VMs on this machine, can you tell?
I have active VMs on this machine, can you tell?
PreLab Q1: What interfaces are available on your machines?
PreLab Q2: Where's WiFi?
PreLab Q3: What's all this other stuff?
In-Lab
First, make a copy of the PostLab Report Document to fill in as you work. Some questions are tagged PostLab. Don't try to do these during the lab session or you will fall behind.
Warning: In general, be careful when sniffing traffic. It can be illegal to monitor communications you were not supposed to have access to.
A. [5 min] Finding and inspecting your own traffic
-
Open a terminal window and run:
ping 4.2.2.2 -
Open wireshark, and start collecting traffic on your default interface.
-
Add a filter:
ip.addr==4.2.2.2 -
You should see something like this:
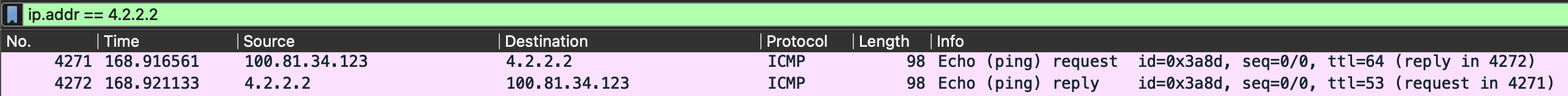
-
Explore a bit in Wireshark, what can you learn about the packet you are observing?
-
Stop the capture. Go to
File → SaveAsand save a copy of this capture to use during your postlab writeup.
PostLab: Document your results.
B: [10 min] Insecure Chat
For this section, we will use the netcat (nc) utility.
If using MacOS or Linux, this is probably already built-in to your machine and can be run from a terminal window.
If using Windows, you can get the ncat tool by installing the nmap package. To run ncat you will need to run Command Prompt as adminstrator.
-
Ensure all of your group's machines are on the same wireless network. You can either connect to the test network
WxIoT-XXXor get public IP addresses for your machine by connecting to UCSD VPN. -
One one machine, set up a “listen” (
nc -l [PORT]) endpoint. -
On another machine, connect to the listening machine (
nc [IP] [PORT]). -
Try typing messages into each endpoint. You should be able to chat!
 What is "localhost"? Why can't you use that?
What is "localhost"? Why can't you use that? -
Start a wireshark capture on all three group member machines (i.e., the sender, the listener, and someone not running netcat).
-
After sending a few messages back and forth, stop and save the captures on all machines.
-
Add a filter so that you are only looking at traffic from your chat session. (Hint: what unique number did you control when you set this chat up?)
-
Which machines can you see your chat traffic in Wireshark? Why?
PostLab: Document your results.
C: [5 min] Discover WiFi Networks Around You
Computers discover WiFi routers using a variety of probe packets. These probe packets contain information such as the name of the WiFi network (SSID), signal strength information, security capabilities, etc.
-
Start a new capture watching the WiFi interface on one of your machines. Since Wireshark doesn't have a direct mechanism to change the capture frequency (channel), we will need to do an indirect capture. On your Mac OS, you should be able to find a tool called
Wireless Diagnostics. Once you open the tool go toWindow -> SnifferHere you should see an option to set theChannelandChannel Width. ChooseChannelas5, leave width unchanged and pressStart. The tool will run a wireless capture till you pressStop. The capture output pcap file can be found in/var/tmp/. This pcap file can be directly opened in Wireshark and analyzed. -
We are running a test network in lab, named something like
WxIoT-fa22. Without connecting to it, can you find it? -
Let this run for about thirty seconds, then stop and save the capture.
-
What are the types of probe packets you can see from our test network?
PostLab: Document your results.
D: [10 min] Snooping Connection Formation
Next, let’s try to capture connection formation between a computer and the wireless router.
-
Start a new capture watching the WiFi interface on two of your machines (one connector, one watcher).
-
Connect one computer to the test wireless network.
-
Once the connection is complete, wait another ten-ish seconds, then stop and save the capture.
-
Start on the machine that you used to make the connection:
-
Filter the traffic to isolate the connection process.
-
What is the first type of packet that the computer sends to the router to initiate connection formation?
-
How do you figure out which packet is sent next? Is there some information in the packet that helps you identify this?
-
How do you know when the connection is established?
-
-
Now look at the connection from the observer's perspective. How much information can you see?
PostLab: Document your results.
E: Extra Credit– Polite WiFi
Warning: This is a fair amount of work. It is truly extra credit.
This is an opportunity to explore further into WiFi operation if you are interested.
A recent paper showed that anyone can force WiFi devices to generate spurious acknowledgement messages, even when they are not connected to the same network.
Using devices you own, replicate this result, and show how to force one of your devices to generate spurious acknowledgements.
PostLab
Go back and fill in the PostLab questions in the PostLab Report Document.
Once you are finished, submit your report via Gradescope.